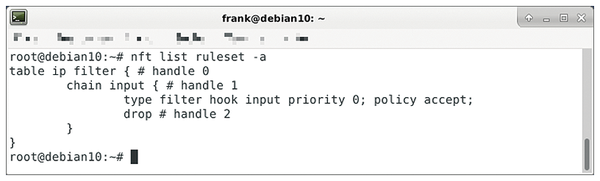
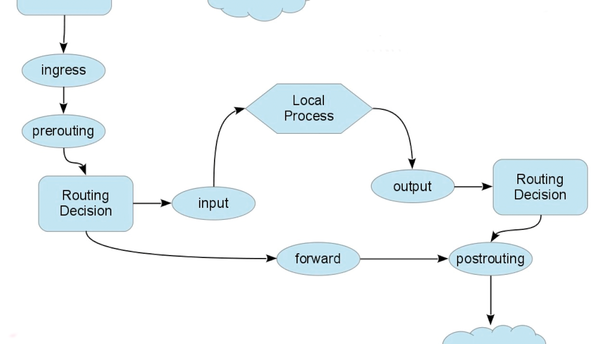
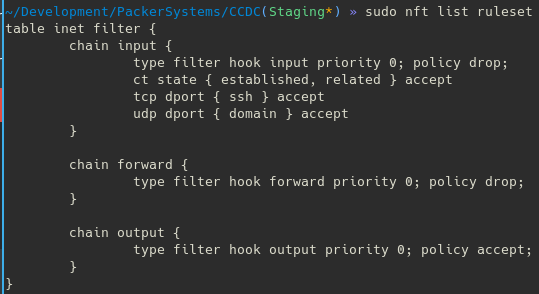
Nft List Table Filter
} this command creates a dynamic set for ipv4 addresses. } chain output { type filter hook output priority 0;
Nft Configuration Scenarios - Ligowave Knowledge Base
For example, running nft list tables i found several default tables like:

Nft list table filter. The linux kernel subsystem is known as nf_tables, and ‘nf’ stands for netfilter. Get input packets add chain inet mytable myin { type filter hook input priority 0; } chain output { type filter hook output priority 0;
# nft add table ip filter; } add a set named denylist to the filter table: Ip protocol tcp tcp dport 80 counter packets 0 bytes 0 # classify set 20:10 ^^^ } } if the whole ruleset is translatable, the users can (re)load it using nft.
} chain forward { type filter hook forward priority 0; To create a new table below the inet family: Ip daddr 8.8.8.8 counter packets 0 bytes 0 tcp dport ssh counter packets 0.
To list a table, use the following commands: Create table inet mytable # add a new base chain: # nft add table inet filter # nft list tables table inet filter.
For example, classify target has not translation: } } but nftables doesn't work correctly. To list existing tables, we shouldn’t have any, we use the following:
# nft list table inet filter table inet filter { } # nft add chain ip filter input { type filter hook input priority 0 \; Ct state invalid counter drop comment early drop of invalid packets ct state {established, related} counter accept comment accept all connections related to connections made by us iif lo accept comment accept loopback iif != lo ip daddr 127.0.0.1/8 counter drop.
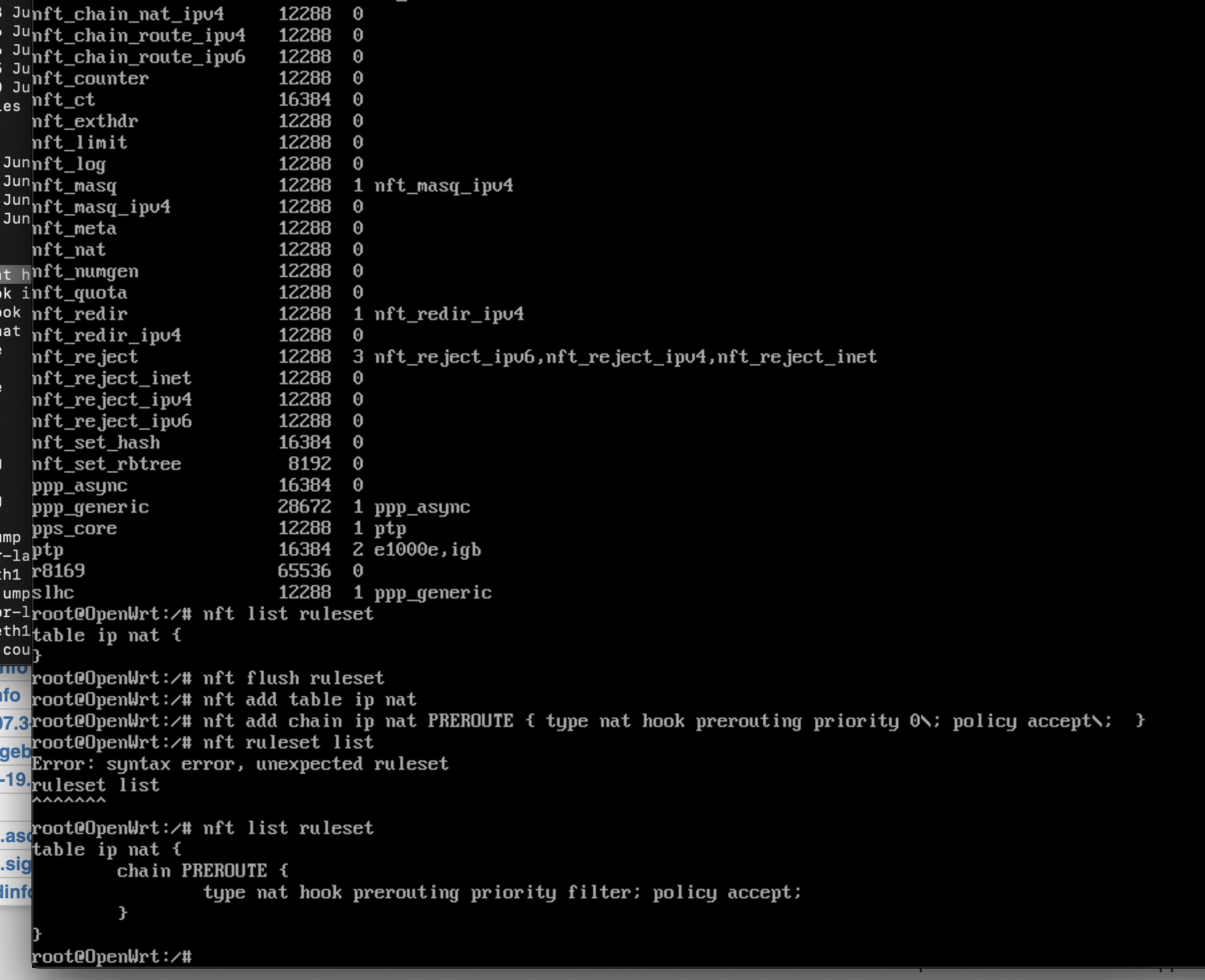
# nft list tables table ip filter table ip6 filter (or a lot) displays all chains set in the specified table. You can list the rules that are contained by a table with the following command: Table ip filter table ip6 filter table bridge filter table ip nat table ip mangle so probably there is something that is applying its policy but i ignore what is.
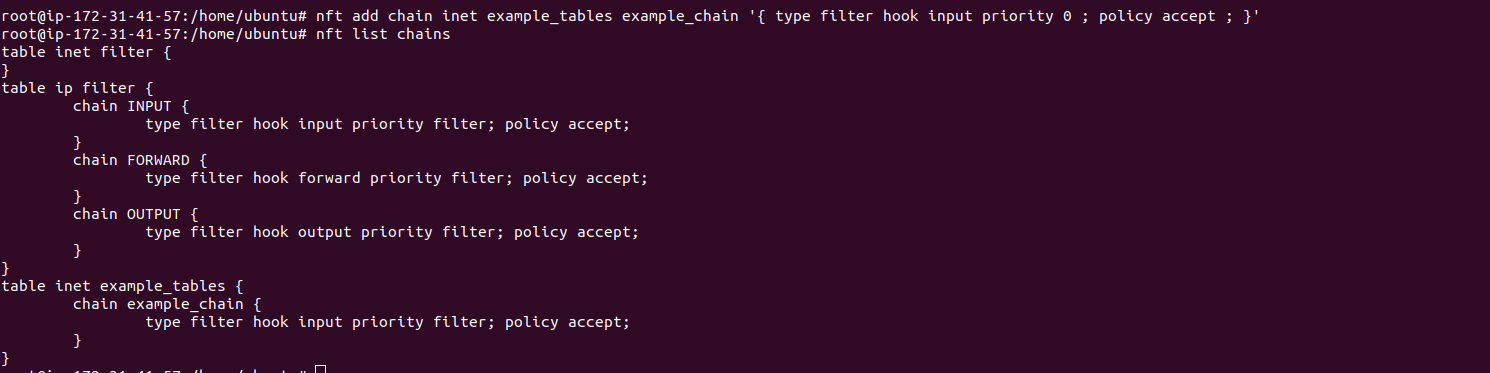
Add the input chain to the filter table: [root@localhost ~]# nft list table inet my_table table inet my_table {chain my_filter_chain</p> Nft is the command line tool used to set up, maintain and inspect packet filtering and classification rules in the linux kernel, in the nftables framework.
% nft list table filter table ip filter { chain input { type filter hook input priority 0; I'm using nftables on debian 10. Nft list table (s) displays only the names of all the tables that have been set.
# nft add set ip filter denylist { type ipv4_addr \; There is my config file. Nft listuse the command to confirm the settings.
The filter table is now created within the inet family but will be empty, it does not contain and chains:

Beginners Guide To Nftables Traffic Filtering - Linux Audit
Nftables 1 Nftables Installation - Computer Outlines Blog

Nftables Part - 2 Live Demo - Youtube
Netfilter Iptablesiptablesnfth File Reference

Beginners Guide To Nftables Traffic Filtering - Linux Audit
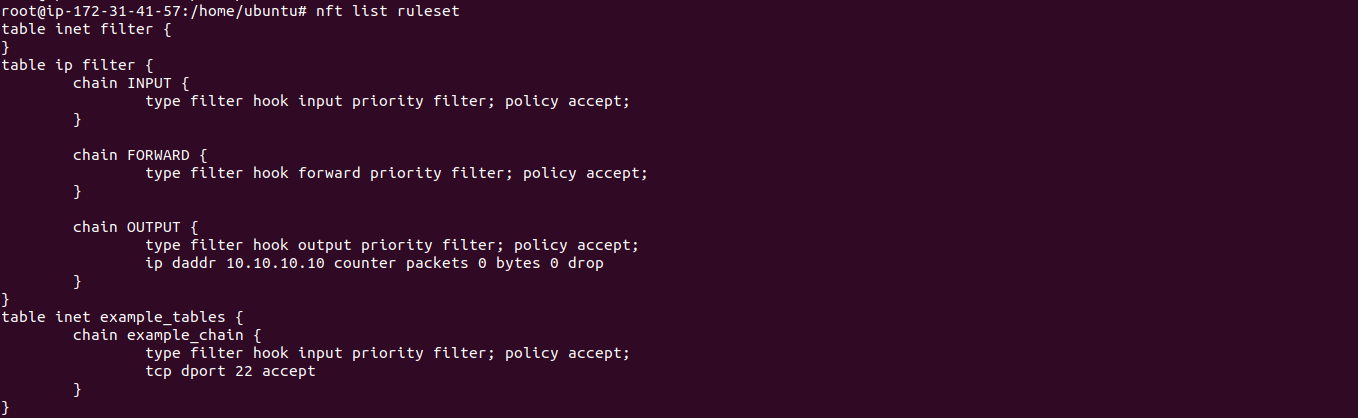
How To Install Nftables On Ubuntu 2004 Lts

Additional Filters Via Nftables
Nftables 1 Nftables Installation - Computer Outlines Blog
Firewalls How To Setup A Basic Firewall Using Ufw Iptables Nftables Or Firewalld - Angry Sysadmins

Using Nftables In Centos 8 And Getting Your Ready For The Rhcsa

Nftables Configure That Linux Firewall Like An Expert
How To Install Nftables On Ubuntu 2004 Lts

Additional Filters Via Nftables
Qos And Nftables Some Findings To Share - 120 By Dlakelan - Network And Wireless Configuration - Openwrt Forum

Securing Your Server With Nftables Datapacketcom